|
|
#1 |
|
Fully Converged
           Posts: 18,163
Karma: 14021202
Join Date: Oct 2002
Location: Switzerland
Device: Too many to count here.
|
eReader DRM Flowchart
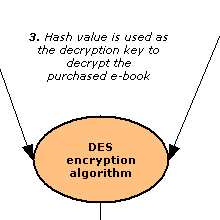 When we discussed Violano's (VP of eReader) view on digital right management (DRM) yesterday, I had the idea to make a flowchart of how eReader DRM appears to work. When we discussed Violano's (VP of eReader) view on digital right management (DRM) yesterday, I had the idea to make a flowchart of how eReader DRM appears to work.You can find the chart attached. I hope it sheds some light... Some important notes that I have also mentioned in the chart: - the hash function applied is a one-way function: the generated output (hash value) is not dependent on the input (credit card number) in any discernible way. Plus, given a hash value, it is computationally unfeasible to find a pre-image (credit card number) that hashes to that value. - the decryption process is continuous; the eReader software doesn't decrypt the entire e-book at once (this would take too long, and total memory twice the size of the e-book). Instead, only blocks of a fixed size are decrypted as the user turns the pages of his book. - the flow chart doesn't show additional steps such as inflating (decompressing) of the e-book. eReader e-books are compressed to reduce the final file size. The inflating process happens on-the-fly after the decryption. - the credit card number is not stored for later decryption; only the computed hash is needed since it is the actual key to the decryption process. - even though the credit card number is not stored on your device, it is stored on ereader.com's database server. A potential hacker may thus obtain this number by hacking the server (in other words, your card number is not 100% safe!). |
|
|

|
|
|
#2 |
|
Technology Mercenary
           Posts: 617
Karma: 2561
Join Date: Feb 2003
Location: East Lyme, CT
Device: Direct Neural Implant
|
If you have a one-way hash, it absolutely cannot be used as a "decryption key" in any way, period. That is why it is called one-way. It cannot be turned around, or reversed, decrypted, or decoded to get the original key back out.
The hash itself, is stored (of course), and any entered "registration" value is hashed using the same method as the first hash, and compared to the stored value. If the two values match, the registration is assumed to be the same as the one that was used to "register" the book in the first place. If they do not match, then it is assumed to be different. You cannot use a one-way hash as a key to decrypt anything. Hashes are encoded, not encrypted. They cannot be "reversed" back into anything. See this informative page for more details with great flowcharts and diagrams. There is also a nice write up on SHA-0 and SHA-1 on Wikipedia. It is computationally infeasible to find any original data with that hash; in fact you can't determine any usable information about the original data with that hash, not even a single bit. For some one-way hash functions it's also computationally impossible to determine two different pieces of data which produce the same hash. |
|
|

|
| Advert | |
|
|
|
|
#3 | |
|
Fully Converged
           Posts: 18,163
Karma: 14021202
Join Date: Oct 2002
Location: Switzerland
Device: Too many to count here.
|
Quote:
1. You take an input ABC. 2. You run ABC through a hash function Hash(ABC) and receive DEF. Note that you ALWAYS receive DEF whenever ABC is given as the input. 3. You use DEF as the key for symmetric encryption/decryption. Note that DEF is of a fixed size, as determined by the hash algorithm. MD5 is 128bit (or 16 bytes) SHA is 160bit (or 20 bytes) SHA-2 is 256bit (or 32 bytes) So let's say you have a cipher that requires a 256bit key (AES for instance). The way to generate a 256bit key is through one of the hashing algorithms that generates a 256bit digest (SHA-2 for instance). So a phrase, a password, or a credit card of any length can be hashed to generate a key of the required size for encrypting data. |
|
|
|

|
|
|
#4 |
|
Is papyrophobic!
           Posts: 1,926
Karma: 1009999
Join Date: Aug 2003
Location: USA
Device: Dell Axim
|
Interesting chart, Alex. Wouldn't it be possible for a hacker to steal the generated hash key code to share the book?
|
|
|

|
|
|
#5 |
|
Fully Converged
           Posts: 18,163
Karma: 14021202
Join Date: Oct 2002
Location: Switzerland
Device: Too many to count here.
|
Hm I think it would be possible... but it wouldn't make much of a difference whether someone shares the hash code or his CC # -- either would identify the original buyer.
|
|
|

|
| Advert | |
|
|
|
|
#6 |
|
Junior Member
 Posts: 4
Karma: 10
Join Date: Jan 2005
Device: dell axim x50v
|
Excellent overview! Great work!
I'm no expert in encryption, so bear with me if I misunderstood some things. According to the principle that only the hash gets stored on the PDA, wouldn't it be possble to give the hash and the ebook to somebody and they "inject" the hash in the settings of their ereader to read the book? This way the other person can read the book, but can't get my CC number because they would have to recompute the hash, correct? The only risk would be that ereader.com could check the hash against their database to see who the original owner was. aCC PS: I'm not planning to give my ebooks to anybody that but find it an interesting topic. |
|
|

|
|
|
#7 |
|
Fully Converged
           Posts: 18,163
Karma: 14021202
Join Date: Oct 2002
Location: Switzerland
Device: Too many to count here.
|
aCC: That is exactly what you could do with the hash; with the same risk you mentioned, that eReader.com could check the hash to find out by whom it was leaked.
Glad you enjoy this overview 
|
|
|

|
|
|
#8 |
|
Junior Member
 Posts: 4
Karma: 10
Join Date: Jan 2005
Device: dell axim x50v
|
That's interesting. Out of interest I checked ereader.com for any disclaimers and I couldn't find anything where it says that you are forbidden to give/sell legally bought ebooks to other people. It would be a grey area because you would still have access to them on the ereader.com, only one person would be allowed to get it, etc. But the borders between legal/illegal are not as clear as I originally thought they were.
As the DRM is not circumvented or reengineered if you pass on the ebook+hash the DMCA can't get you on those terms. So theoretically you could even sell your books again or give them to friends after you've finished them. What I find useful is that you could back up all your ebooks with the corresponding hashes and not worry about your old visa numbers. Maybe someone will write small import/export tool that makes this easy. :-) aCC |
|
|

|
|
|
#9 |
|
Fully Converged
           Posts: 18,163
Karma: 14021202
Join Date: Oct 2002
Location: Switzerland
Device: Too many to count here.
|
Interesting idea. Your CC # should be safe even when you give out the hash code (due to the one-way nature of the hash). And since you bought the e-book, you should be able, similar to paper books, to resell them, right?
We should think about this some more... |
|
|

|
 |
«
Previous Thread
|
Next Thread
»
|
 Similar Threads
Similar Threads
|
||||
| Thread | Thread Starter | Forum | Replies | Last Post |
| EReader DRM coming soon? | luqmaninbmore | Astak EZReader | 10 | 11-06-2009 06:35 PM |
| Beginning to think that Ereader DRM will not happen | cvkemp | Astak EZReader | 28 | 10-22-2009 06:23 PM |
| mobipocket/ereader DRM | PieOPah | Kindle Formats | 4 | 07-17-2009 04:06 PM |
| eReader sales and DRM questions | Richard Maseles | Other formats | 3 | 01-07-2009 04:07 AM |
| DRM-free Mobi to eReader? | tcv | Workshop | 8 | 10-16-2008 05:47 PM |
All times are GMT -4. The time now is 04:26 AM.


